单条日志清理
参考三好大佬的文章
https://3gstudent.github.io/Windows-XML-Event-Log-(EVTX)%E5%8D%95%E6%9D%A1%E6%97%A5%E5%BF%97%E6%B8%85%E9%99%A4-%E4%B8%80-%E5%88%A0%E9%99%A4%E6%80%9D%E8%B7%AF%E4%B8%8E%E5%AE%9E%E4%BE%8B
evtx基础知识
参考https://github.com/libyal/libevtx/blob/main/documentation/Windows XML Event Log (EVTX).asciidoc
evtx文件结构包含3部分
- file header
- chunks
- trailing empty values
https://github.com/libyal/libevtx/blob/main/documentation/Windows%20XML%20Event%20Log%20(EVTX).asciidoc#2-file-header
chunks
https://github.com/libyal/libevtx/blob/main/documentation/Windows%20XML%20Event%20Log%20(EVTX).asciidoc#3-chunk
trailing empty values
https://github.com/libyal/libevtx/blob/master/documentation/Windows%20XML%20Event%20Log%20%28EVTX%29.asciidoc#32-event-record
具体操作
查看日志文件

这里要删除的记录为1915
删除后效果如下

可以使用该工具 https://github.com/williballenthin/python-evtx
python evtx_record_structure.py System.evtx 1915

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
| C:\Users\TEST\Desktop>python evtx_record_structure.py System.evtx 1915
00000000: 2A 2A 00 00 38 01 00 00 7B 07 00 00 00 00 00 00 **..8...{.......
00000010: 23 EB 07 A2 D4 FB D3 01 0F 01 01 00 0C 01 65 CE #.............e.
00000020: 1B C7 EE 0D 00 00 14 00 00 00 01 00 04 00 01 00 ................
00000030: 04 00 02 00 06 00 02 00 06 00 02 00 06 00 08 00 ................
00000040: 15 00 08 00 11 00 00 00 00 00 04 00 08 00 04 00 ................
00000050: 08 00 08 00 0A 00 01 00 04 00 00 00 00 00 00 00 ................
00000060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000070: 00 00 00 00 00 00 8B 00 21 00 04 00 00 00 7C 1B ........!.....|.
00000080: 00 40 00 00 00 00 00 00 80 80 23 EB 07 A2 D4 FB .@........#.....
00000090: D3 01 D8 01 00 00 9C 07 00 00 7B 07 00 00 00 00 ..........{.....
000000A0: 00 00 00 0F 01 01 00 0C 01 DE E1 DC 34 6C 11 00 ............4l..
000000B0: 00 04 00 00 00 4E 00 01 00 08 00 01 00 04 00 08 .....N..........
000000C0: 00 0E 00 0E 00 42 00 61 00 63 00 6B 00 67 00 72 .....B.a.c.k.g.r
000000D0: 00 6F 00 75 00 6E 00 64 00 20 00 49 00 6E 00 74 .o.u.n.d. .I.n.t
000000E0: 00 65 00 6C 00 6C 00 69 00 67 00 65 00 6E 00 74 .e.l.l.i.g.e.n.t
000000F0: 00 20 00 54 00 72 00 61 00 6E 00 73 00 66 00 65 . .T.r.a.n.s.f.e
00000100: 00 72 00 20 00 53 00 65 00 72 00 76 00 69 00 63 .r. .S.e.r.v.i.c
00000110: 00 65 00 63 6B 28 57 D0 8F 4C 88 0E 00 00 00 42 .e.ck(W..L.....B
00000120: 00 49 00 54 00 53 00 2F 00 34 00 00 00 00 00 00 .I.T.S./.4......
00000130: 15 00 00 00 38 01 00 00 ....8...
record(absolute_offset=8776)
RootNode(offset=0x18)
StreamStartNode(offset=0x18)
TemplateInstanceNode(offset=0x1c, resident=False)
Substitutions(offset=0x26)
UnsignedByteTypeNode(offset=0x7a) --> 4
UnsignedByteTypeNode(offset=0x7b) --> 0
UnsignedWordTypeNode(offset=0x7c) --> 0
UnsignedWordTypeNode(offset=0x7e) --> 7036
UnsignedWordTypeNode(offset=0x80) --> 16384
Hex64TypeNode(offset=0x82) --> 0x8080000000000000
FiletimeTypeNode(offset=0x8a) --> 2018-06-04 07:21:19.394281
NullTypeNode(offset=0x92)
UnsignedDwordTypeNode(offset=0x92) --> 472
UnsignedDwordTypeNode(offset=0x96) --> 1948
UnsignedQwordTypeNode(offset=0x9a) --> 1915
UnsignedByteTypeNode(offset=0xa2) --> 0
NullTypeNode(offset=0xa3)
NullTypeNode(offset=0xa3)
NullTypeNode(offset=0xa3)
NullTypeNode(offset=0xa3)
NullTypeNode(offset=0xa3)
NullTypeNode(offset=0xa3)
NullTypeNode(offset=0xa3)
BXmlTypeNode(offset=0xa3) -->
RootNode(offset=0xa3)
StreamStartNode(offset=0xa3)
TemplateInstanceNode(offset=0xa7, resident=False)
Substitutions(offset=0xb1)
WstringTypeNode(offset=0xc5) --> Background Intelligent Transfer Servi
ce
WstringTypeNode(offset=0x113) --> 正在运行
UnsignedDwordTypeNode(offset=0x11b) --> 14
BinaryTypeNode(offset=0x11f) --> QgBJAFQAUwAvADQAAAA=
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"><System><Pr
ovider Name="Service Control Manager" Guid="{555908d1-a6d7-4695-8e1e-26931d2012f
4}" EventSourceName="Service Control Manager"></Provider>
<EventID Qualifiers="16384">7036</EventID>
<Version>0</Version>
<Level>4</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x8080000000000000</Keywords>
<TimeCreated SystemTime="2018-06-04 07:21:19.394281"></TimeCreated>
<EventRecordID>1915</EventRecordID>
<Correlation ActivityID="" RelatedActivityID=""></Correlation>
<Execution ProcessID="472" ThreadID="1948"></Execution>
<Channel>System</Channel>
<Computer>WIN-E8C6J8CN50O</Computer>
<Security UserID=""></Security>
</System>
<EventData><Data Name="param1">Background Intelligent Transfer Service</Data>
<Data Name="param2">正在运行</Data>
<Binary>QgBJAFQAUwAvADQAAAA=</Binary>
</EventData>
</Event>
|
删除单条日志思路——覆盖
修改日志 Event Record
size长度,然后覆盖掉下一条日志,这样windows在解析日志时,下一条日志就会被隐藏,从而实现所谓的单条目录的删除
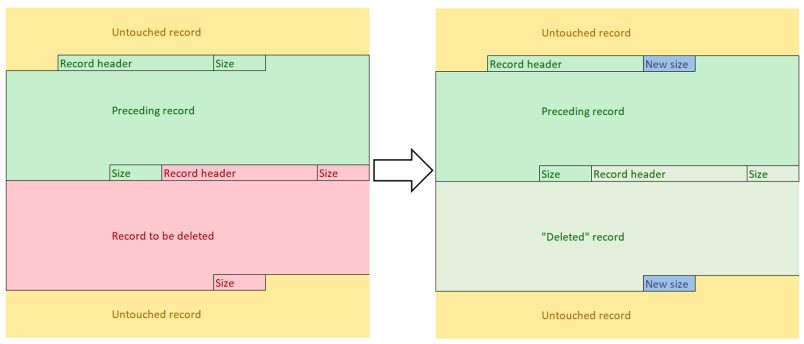 从大佬那里抄的图
从大佬那里抄的图
具体方法:
1.file header中的Next record identifier减一
2.重新计算file header 中的 chunksum
3.修改Event Record:
重新计算待删除Event Record前后长度,更新后续Event Record的Event
record identifier
4.更新ElfChnk,
删除单条日志的实例
实例样本
https://github.com/3gstudent/Eventlogedit-evtx--Evolution/blob/master/System.evtx
这里采用小端序 0x077c 减一后为 0x77b
 修改后
修改后
重新计算checksum值
 原值
原值
计算前120bytes 的 CRC32,直接引用大佬的脚本
1
2
3
4
5
6
| import binascii
def crc2hex(crc):
return '%08x' % (binascii.crc32(binascii.a2b_hex(crc)) & 0xffffffff)
d='456C6646696C6500000000000000000000000000000000007B0700000000000080000000010003000010010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000'
print(crc2hex(d)
|
得到结果为 ccc94756 然后进行替换

修改Event Record
重新计算待删除Event
Record前后长度,更新后续Event Record的Event record identifier

Event record头为 0x2a\0x2a\0x00\0x00 在010editor搜索一下 找到Event
record头
途中的 0x0778 对应值为 1912 这个是日志中的第一条日志,这里要删除1915
那么去找到 0x077b值对应的EventRecord(第四条日志)
 第四条日志
第四条日志
长度为 0x0138h EventRecord ID 为 0x77bh(1915)
结尾处的值为EventRecord 长度 0x138h
在后面需要覆盖后也要修改这个值
再找到第三条日志

长度为 0x0480h EventRecord ID为 0x77ah (1914)
找到两条日志后 修改一下 第三条日志的长度 使其覆盖掉第四条日志
New_legth = 0x138h+0x480h=0x5b8h

然后更新第四条日志最后面的长度 从0x138h 改为 0x5b8h

更新ElfChnk


https://github.com/libyal/libevtx/blob/main/documentation/Windows%20XML%20Event%20Log%20(EVTX).asciidoc#31-chunk-header
在测试日志中只有一个Elfchnk 但别的可能会有多个ElfChnk 需要找到对应的
ElfChnk

修改last Event record number 0x04h -1 = 0x03h
修改last Event record identifier 0x77bh -1 = 0x77ah
修改Last event record data offset 0x1248h =>
0xDC8h
为第三条Event Record(最后一条)相对于ElfChuk的偏移长度
ElfChnk 为 0x1000h 第三条开始位置为 0x1DC8h 所以偏移量为 0xDC8h
修改Event records checksum 0xD3D3DE43h =>
0xF92FEDB9h
Event records checksum 为所有Event records 的校验和
这里需要计算三条的
计算过程 抽时间算一下
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~`
计算后为 0xF92FEDB9h
修改Checksum 0xEB4C47BFh => 0x3CE0BF8h
计算前120 和128-512 处的CRC32值 结果为 0x3CE0BF8h

另存后打开 可以看到 第四条我们想要删除的日志已经成功隐藏

















